Cybersecurity
Energy Hub
Work with facility IT System Administrators to ensure that the system adheres to the site-specific cybersecurity policies.
Energy Hub is a cloud-based SaaS application with data hosted in a secure, ISO27001-certified Tier III Microsoft cloud service data center. For more information on Microsoft cloud services security, visit the Microsoft Trust Portal.
Energy Hub includes many operational security features, such as
- Strong password enforcement
- (Optional) Two-factor authentication
- Role-based access control
- Session timeout after a period of inactivity
Regular security updates are automatically applied to the Energy Hub cloud servers without user interaction.
All data for Energy Hub is transmitted through IoT gateways that comply with ISA/IEC 62443 cybersecurity standards. This ensures end-to-end security from gateway to cloud, guaranteeing that all data comes from trusted sources. The gateways use secure protocols for data transmission. Here are some characteristics of the secure data collection:
- Data transmission between the on-site gateways and the Schneider Electric cloud services uses MQTT protocol and is encrypted using TLS 1.2 (HTTPS).
- Only device measurement data and events are sent to the cloud services.
- Only the gateway can start the connection with the cloud services. Data flow during transmission can be bi-directional.
To log in to Energy Hub, users need a Schneider Electric ID, a unique identifier used across multiple Schneider Electric products and services. This ID is part of the Schneider Electric Customer Identity and Access Management System, which centralizes policies and technologies for authentication and authorization.
In Energy Hub, each user is assigned a role and access permissions that define their actions and data access. Access permissions can be set for an entire organization or limited to specific locations within it, determining what data a user can access.
Below is a list of user roles and their capabilities:
| Role | Description |
|---|---|
| Viewer | A Viewer, can only view information. |
| Operator | An Operator, can view information and do limited setup. |
| Admin | An Admin, can view information and do all setup. |
| Engineer | An Engineer, can view information and do limited setup. |
| Support | Support can view information and do limited setup. |
Energy Hub automatically ends inactive sessions after a set time interval. Users are reminded of the timeout and can choose to continue the session, which resets the timeout counter. The timeout interval is not configurable.
The following diagram and table identify the major components of an Energy Hub system and provide relevant cybersecurity information for each component:
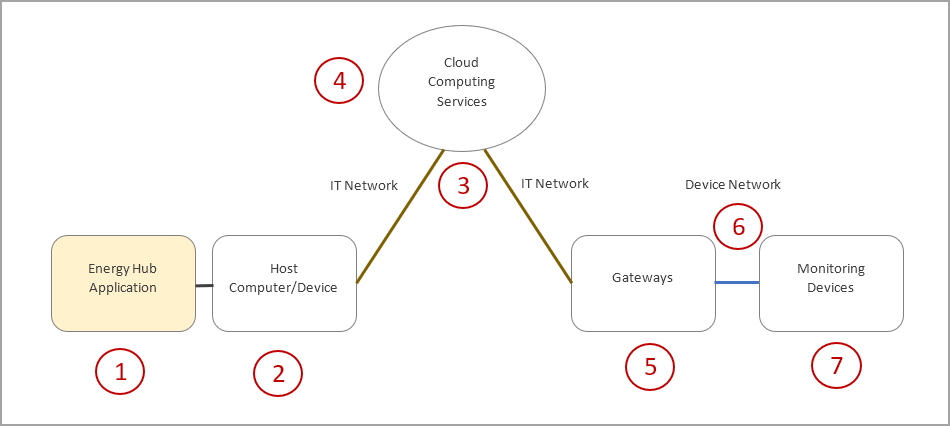
| Area | Feature | Details |
|---|---|---|
| 1 | Energy Hub user access |
A user in Energy Hub is a logical entity that provides access to the system. It controls what a person can do and which data they can access. Unauthorized access to Energy Hub could compromise the system integrity and data accuracy, and it could disclose sensitive information, such as operational or facility details. To reduce cybersecurity risks:
NOTE: Energy Hub automatically ends inactive web app sessions after 10 minutes. Before the session is ended, you are reminded of the timeout with the option to continue the session. If you select to continue the session, the timeout counter resets. The 10 minute timeout interval is not configurable. See Users for information on how to set up and maintain users in Energy Hub. |
| 2 | Host computers and mobile devices |
Use general best practices to secure your computers, mobile devices, and software. To reduce cybersecurity risks:
|
| 3 | IT networks |
Secure your IT networks. Get expert help and advice to deploy and maintain the right network architectures and cybersecurity measures for your organization. |
| 4 | Cloud services |
No end user actions are required. Schneider Electric partners with cloud service providers who use industry-leading, ISO/IEC 27001 compliant cybersecurity solutions to protect cloud resources. |
| 5 | Device gateways |
Keep your device gateways secure. Follow the cybersecurity guidelines provided with your gateway devices. |
| 6 | Device networks |
Secure your device networks. Get expert help and advice to deploy and maintain the right network architectures and security measures for your organization. |
| 7 | Monitoring devices |
Keep your monitoring devices secure. Follow the cybersecurity guidelines provided with your monitoring devices. |
The IoT gateways require an internet connection to send data to Energy Hub. They transmit all data over HTTPS using the same ports on the network firewall as standard web browsers, making Energy Hub easy to integrate into your IT network.
Typically, you encounter one of the following scenarios:
- No special configuration is needed and the gateways simply connect to the cloud services.
- The network uses a proxy server to access the internet. In this case, you need to configure the gateways with the proxy server settings, using the gateway setup webpage.
- The network uses a firewall that needs to be configured to allow the gateways to access the cloud services (also called endpoints). See the list of required endpoints below.
The following shows a list of endpoints that must be accessible to the IoT gateways:
EcoStruxure Panel Server
| Endpoint | Protocol/Port | Description |
|---|---|---|
cbBootStrap.gl.StruXureWareCloud.com
|
HTTPS / 443 |
Used to authenticate and register Panel Server. This is needed for the initial start-up or after a factory reset. |
etp.prod.StruXureWareCloud.com
|
HTTPS / 443 |
Used to send firmware updates from the cloud server to Panel Server. |
cnm-ih-na.azure-devices.net
*.azure-devices.net
|
HTTPS / 443 |
Used for communication between Panel Server and cloud server, for example to send configuration, measurement, or alarm data. |
time.gl.StruXureWareCloud.com
|
NTP (UDP 123) |
Used for Panel Server clock synchronization. |
RemoteShell.rsp.Schneider-Electric.com
|
HTTPS / 443 |
Used by the Schneider Electric Customer Care Center to remotely access Panel Server webpages, if needed. |
cnmiothubappstna.blob.core.windows.net/file-upload
|
HTTPS / 443 |
Used to send large site topologies (>250kB) from Panel Server to the cloud server. |
cnmdapiappstna.blob.core.windows.net
|
HTTPS / 443 |
Used by Panel Server to send logs and diagnostics files to the cloud server, if requested by the Schneider Customer Care Center. |
EcoStruxure Site Server
| Endpoint | Protocol/Port | Description |
|---|---|---|
powercloud.se.com
|
HTTPS / 443 |
Used to authenticate and register Site Server. This is needed for the initial start-up or after a factory reset. |
cnmiothubappstna.blob.core.windows.net
|
HTTPS / 443 |
Used to send site topologies from Site Server to the cloud server. |
cnm-ih-na.azure-devices.net
|
HTTPS / 443 |
Used for communication between Site Server and cloud server, for example to send configuration, measurement, or alarm data. |
schneider-electric-fno.flexnetoperations.com
|
HTTPS / 443 |
Used for Site Server license checks. These checks are performed daily to confirm that the gateway has a valid license. |
Schneider Electric
Energy Hub collects operational energy system data and a small amount of personally identifiable information (PII), such as user names and email addresses provided during registration. Schneider Electric is committed to protecting customer data confidentiality and security. Energy Hub adheres to Schneider Electric's global cybersecurity and data protection policies.
Energy Hub is developed using secure lifecycle practices based on ISO/IEC 27000-series standards for information security. This ensures security is integrated from the start, not as an afterthought.
Examples of our secure development lifecycle practices include::
- Periodic authorized simulated cyberattacks (penetration tests) on Energy Hub, performed by Schneider Electric cybersecurity specialists to evaluate the security of the system.
- Ongoing cybersecurity threat modeling and analysis by development teams for Energy Hub.
- Ongoing cybersecurity and data privacy training for all Energy Hub designers and developers.
Our global operations team continuously monitors Energy Hub for security threats. Automated intrusion detection systems track data traffic and log all activity. We regularly conduct penetration testing and are prepared to manage vulnerabilities effectively in case of a cybersecurity incident. We have documented and tested procedures for quick system recovery.
For security notifications or bulletins, to report a potential vulnerability, or to learn about how Schneider Electric manages vulnerabilities, see Cybersecurity Support Portal (Schneider Electric website).
For additional cybersecurity related information, see cybersecurity resources.
 warning
warning